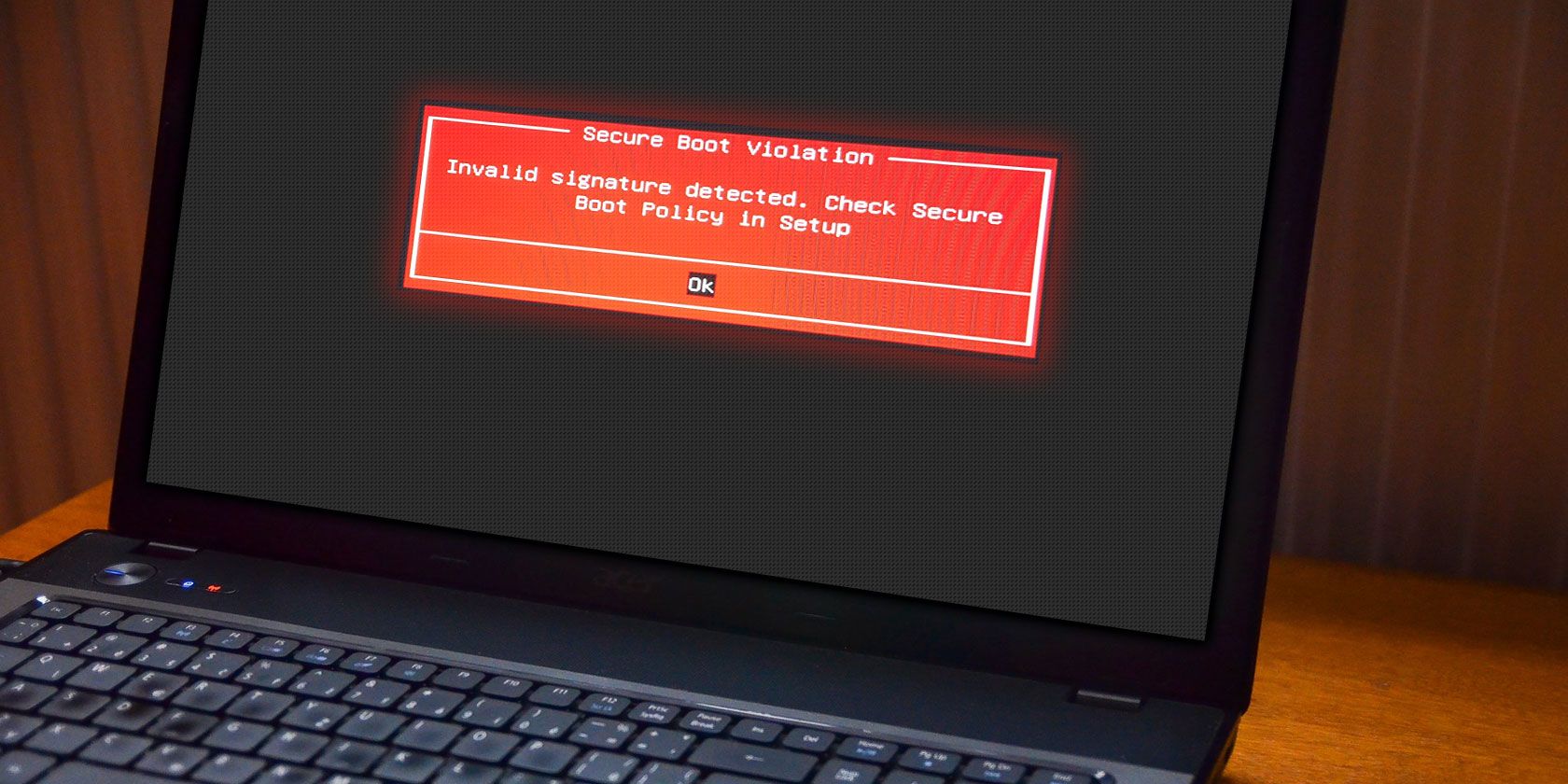
Have you ever tried to install a second operating system alongside Windows? Depending on the OS, you might have encountered the UEFI Secure Boot feature.
If Secure Boot doesn’t recognize the code you’re trying to install, it will stop you. Secure Boot is handy for preventing malicious code running on your system. But it also stops you booting some legitimate operating systems, like Kali Linux, Android x86, or TAILS.
But there is a way around it. This short guide will show you how to disable UEFI Secure Boot to let you dual boot any operating system you like.
What Is UEFI Secure Boot?
Let’s take a second to consider precisely how Secure Boot keeps your system safe.
Secure Boot is a feature of the Unified Extensible Firmware Interface (UEFI). UEFI itself is the replacement for the BIOS interface found on many devices. UEFI is a more advanced firmware interface with many more customization and technical options.

Secure Boot is something of a security gate. It analyzes code before you execute it on your system. If the code has a valid digital signature, Secure Boot lets it through the gate. If the code has an unrecognized digital signature, Secure Boot blocks it from running, and the system will require a restart.
At times, code that you know is safe, and comes from a reliable source, might not have a digital signature in the Secure Boot database.
For example, you can download numerous Linux distributions directly from their developer site, even verifying the distribution checksum to check for tampering. But even with that confirmation, Secure Boot will still reject some operating systems and other types of code (such as drivers and hardware).
How to Disable Secure Boot
Now, I don’t advise disabling Secure Boot lightly. It really does keep you safe (check out the Secure Boot vs. NotPetya Ransomware video below, for example), especially from some of the nastier malware variants like rootkits and bootkits (others would contend it was the security measure to stop Windows pirating). That said, sometimes it gets in the way.
Please note that turning Secure Boot back on may require a BIOS reset. This does not cause your system to lose any data. It does, however, remove any custom BIOS settings. Moreover, there are some examples where users are permanently no longer able to turn on Secure Boot, so please bear that in mind.
Okay, here’s what you do:
- Turn your computer off. Then, turn it back on and press the BIOS entry key during the boot process. This varies between hardware types, but is generally F1, F2, F12, Esc, or Del; Windows users can hold Shift while selecting Restart to enter the Advanced Boot Menu. Then select Troubleshoot > Advanced Options: UEFI Firmware Settings.
- Find the Secure Boot option. If possible, set it to Disabled. It is usually found in the Security tab, Boot tab, or Authentication tab.
- Save and Exit. Your system will reboot.
You have successfully disabled Secure Boot. Feel free you grab your nearest previously unbootable USB drive and finally explore the operating system. Our list of the best Linux distributions is a great place to start!
How to Re-Enable Secure Boot
Of course, you might want to turn Secure Boot back on. After all, it does help protect against malware and other unauthorized code. If you directly install an unsigned operating system, you’ll need to remove all traces before attempting to turn Secure Boot back on. Otherwise, the process will fail.
- Uninstall any unsigned operating systems or hardware installed when Secure Boot was disabled.
- Turn your computer off. Then, turn it back on and press the BIOS entry key during the boot process, as above.
- Find the Secure Boot option and set it to Enabled.
- If Secure Boot doesn’t enable, try to Reset your BIOS to factory settings. Once you restore factory settings, attempt to enable Secure Boot again.
- Save and Exit. Your system will reboot.
- In the event the system fails to boot, disable Secure Boot again.
Troubleshooting Secure Boot Enable Failure
There are a few small fixes we can try to get your system booting with Secure Boot enabled.
- Make sure to turn UEFI settings on in the BIOS menu; this also means making sure Legacy Boot Mode and equivalents are off.
- Check your drive partition type. UEFI requires GPT partition style, rather than the MBR used by Legacy BIOS setups. To do this, type Computer Management in your Windows Start menu search bar and select the best match. Select Disk Management from the menu. Now, find your primary drive, right-click, and select Properties. Now, select the Volume. Your partition style is listed here. (If you need to switch from MBR to GPT there is only one option to change the partition style: back up your data and wipe the drive.)
- Some firmware managers have the option to Restore Factory Keys, usually found in the same tab as the other Secure Boot options. If you have this option, restore the Secure Boot factory keys. Then Save and Exit, and reboot.

Trusted Boot
Trusted Boot picks up where Secure Boot stops, but really only applies to the Windows 10 digital signature. Once UEFI Secure Boot passes the baton, Trusted Boot verifies every other aspect of Windows, including drivers, startup files, and more.
Much like Secure Boot, if Trusted Boot finds a corrupted or malicious component, it refuses to load. However, unlike Secure Boot, Trusted Boot can at times automatically repair the issue at hand, depending on the severity. The below image explains a little more about where Secure Boot and Trusted Boot fit together in the Windows boot process.

Should You Turn Off Secure Boot?
Disabling Secure Boot is somewhat risky. Depending on who you ask, you’re potentially putting your system security at risk.
Secure Boot is arguably more useful than ever at the current time. Bootloader attacking ransomware is very real. Rootkits and other particularly nasty malware variants are also out in the wild. Secure Boot provides UEFI systems with an extra level of system validation to give you peace of mind.
Read the full article: How to Disable UEFI Secure Boot to Dual Boot Any System
from MakeUseOf https://ift.tt/2GL6e4m
via IFTTT
No comments:
Post a Comment