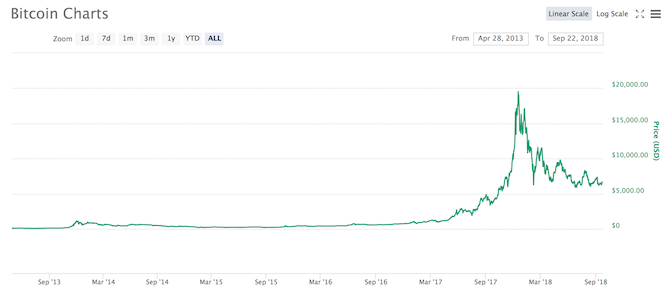
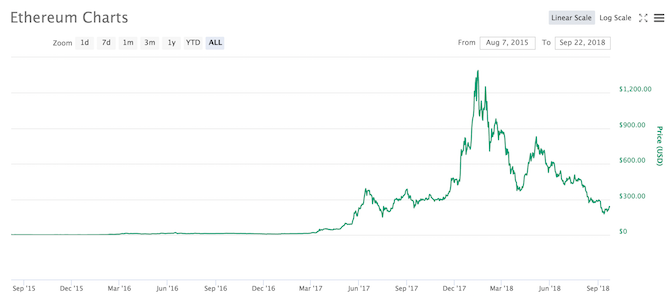
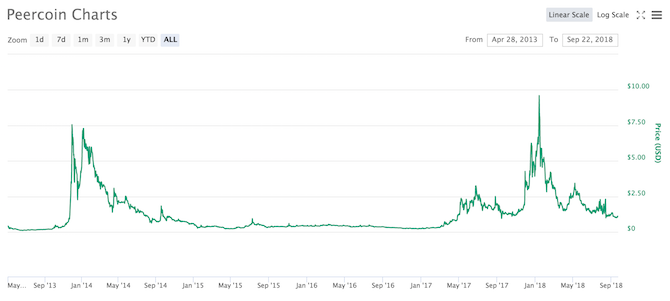
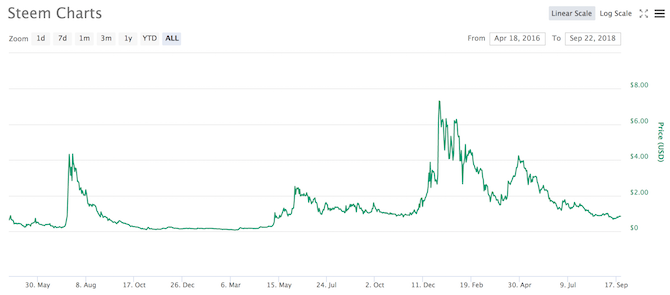
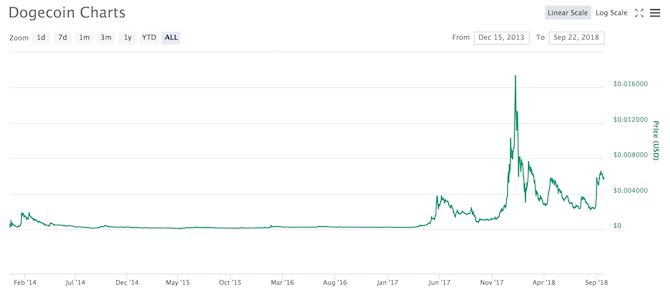
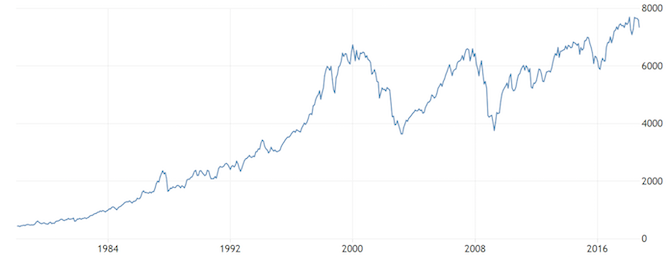
Did you ride the peaks of the bitcoin wave, or did you wait for the trough to hit the shore? When bitcoin was touching $20,000 per coin, everyone was an expert or potential investor. Prices are now more unpredictable, making it harder for would-be investors to make a profit.
Given cryptocurrencies straddle the median between currency and commodity, there is money to be made—but only if you know what you are doing. Check out these risk-free cryptocurrency market simulators before splashing your cash on the real deal.
1. Bitcoin Mining Profit Calculator
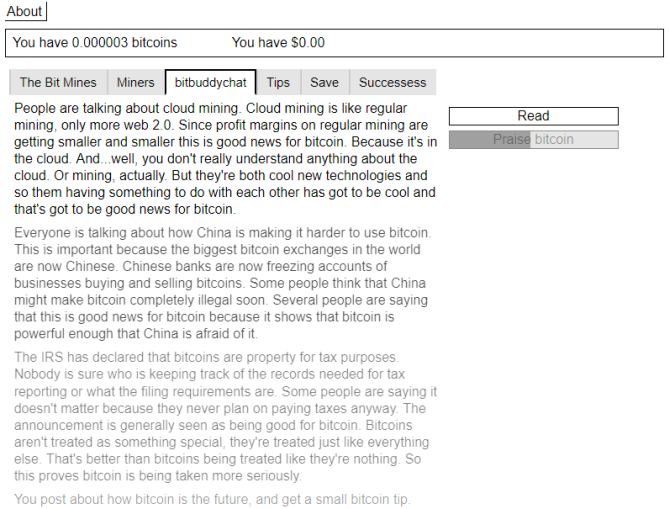
The Bitcoin Mining Profit Calculator (BMPC) is a great starting point if you are completely new to bitcoin and cryptocurrency. It’s a lot more than a simple trading simulator since it includes a full introduction to bitcoin too.
The website works like an interactive fiction-come-idle clicker game. BMPC updates with new tabs and explanations as you click different prompts on the screen, thus making different choices. Don’t worry, you won’t miss out on any pertinent information, but it will make you aware of the kind of news that affects bitcoin’s prices as well as the inner workings of the bitcoin community.
BMPC is nothing great to look at and plays like a text adventure, but there’s nothing wrong with that. This is meant to be an educational game rather than an entertaining one.
2. Bitcoin Hero
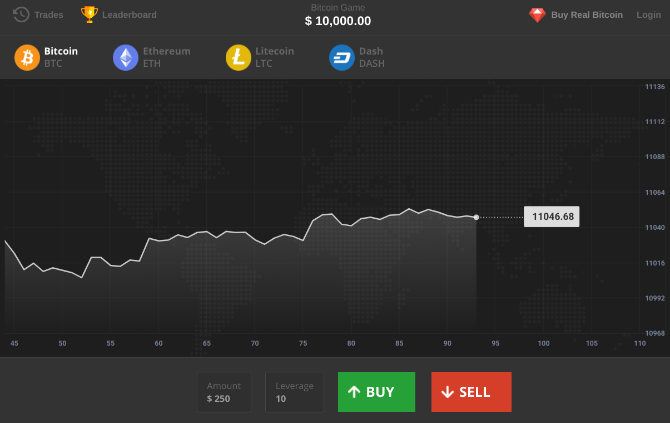
For those who don’t need a tutorial in what cryptocurrency is and want to jump right in, Bitcoin Hero is excellent. The web app works fine on mobile screens as well, so you can enjoy the game without ever installing it, but there is an Android app.
While it isn’t necessary to install Bitcoin Hero, you’ll want to create an account to track your progress over multiple sessions. You start with $10,000 in your wallet, and you can buy and sell four cryptocurrencies: Bitcoin, Ethereum, Litecoin, and Dash. The cryptocurrency prices come straight from the real world, so its akin to the real thing.
3. Altcoin Fantasy
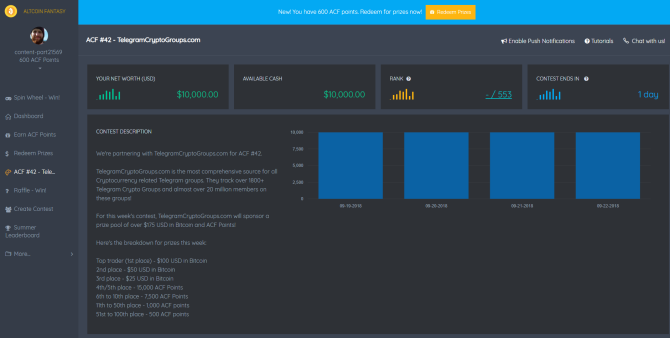
Altcoin Fantasy (ACF) steps up where Bitcoin Hero ends. Unlike Bitcoin Hero, Altcoin Fantasy lets you trade against other people, in competition, for a range of real-life prizes. For instance, a prize in a recent ACF contest was $100 worth of Bitcoin!
Competing also earns in-game currency, ACF Points, which you can trade in for real-life prizes, like a CryptoKitty or a 12-month subscription to TradingView. There’s also a daily sign-in bonus and a free spin-wheel for more points!
ACF ramps up the realism by using real-world market from a range of exchanges, differing between competitions. There’s usually a healthy amount of competition too, so you will need to sharpen your crypto market analysis skills to hit the head of the pack. Starting out with $10,000, you have a decent bank account to make a profit from.
Another thing I like about Altcoin Fantasy is its Private Contest mode. You can set up a 14-day contest for you and your buddies to see who has the best crypto-trading chops—and then brag about it when you win, of course. You can even set an entry fee.
4. eToro
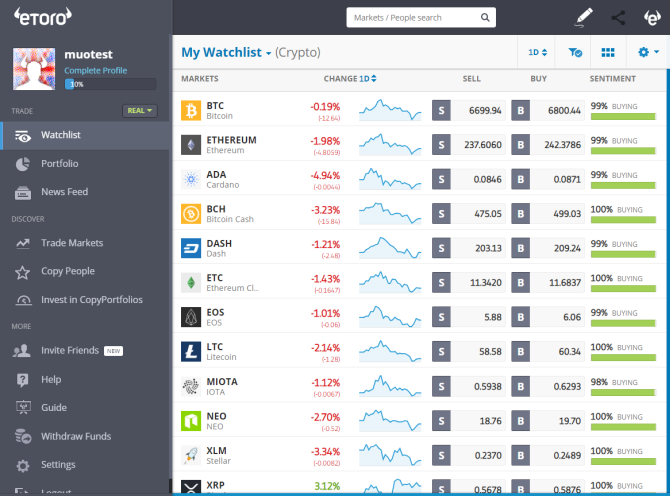
eToro is a social trading app that has captured the imagination of regular investors and professionals alike. You find profitable investors that match your level of risk, and then copy their trades as they execute them. There are thousands of profitable traders and decent money to be made.
However, if you don’t want to risk your money and want to learn before opening your wallet, sign up for an eToro practice account here. Your free account comes with up to $100,000 for trading so you can really go to town with your practice trades.
5. CoinMarketGame
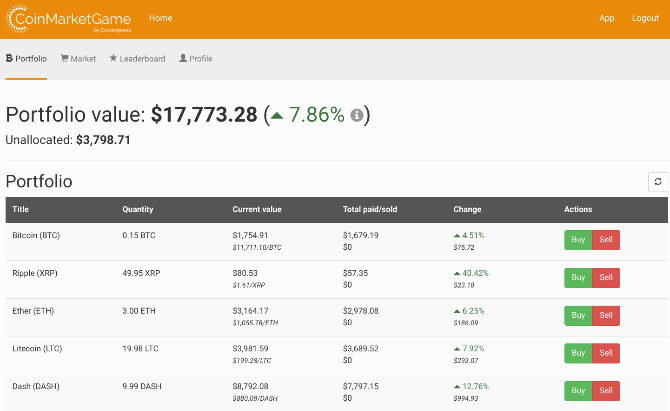
For a full-fledged simulator consisting of all major cryptocurrencies, you can’t do much better than CoinMarketGame. It does all the basics right to deliver an accurate experience of what it’s like to be a trader in this market.
Sign up for an account to receive a $20,000 starting pot. Spend it wisely by building a diverse portfolio, investing in both popular and less-known altcoins with high growth potential. You can check the leaderboard out and see what your competitors are trading, then head back to the markets to see how they maximize their crypto trading profits.
6. Spark Profit
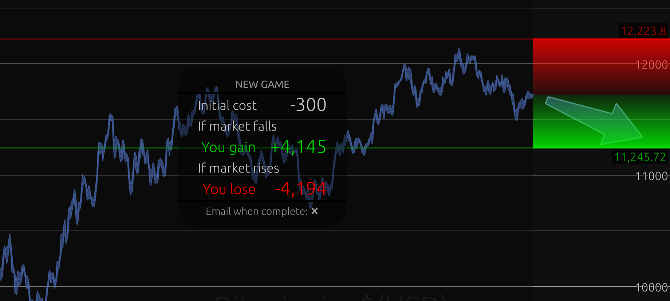
Spark Profit is a crypto prediction game for Android, iOS, and your browser. You use historical crypto data to predict the position of Bitcoin, Ethereum, and Litecoin, as well as several international stock markets. Spark Profit is basically about taking a long or short position on the future of the market. Your goal is to win points with accurate predictions. If the market touches your profit price, you win points. If it hits your loss point, you lose them. Simple, right?
Your goal is to win points. Estimate and set a profit price that you think the market will hit. Also, set a loss price while you’re at it. If the market touches the profit price, you will win points, but touching the loss price will make you lose points. Simple, right?
Spark Profit is a lot tougher than it sounds, and the much-needed reality check that early investors need. Before you invest a single dollar in cryptocurrencies, play this game and see how well you do. If you end up bankrupt, you’re better off putting your money back in your wallet.
7. Bitmex
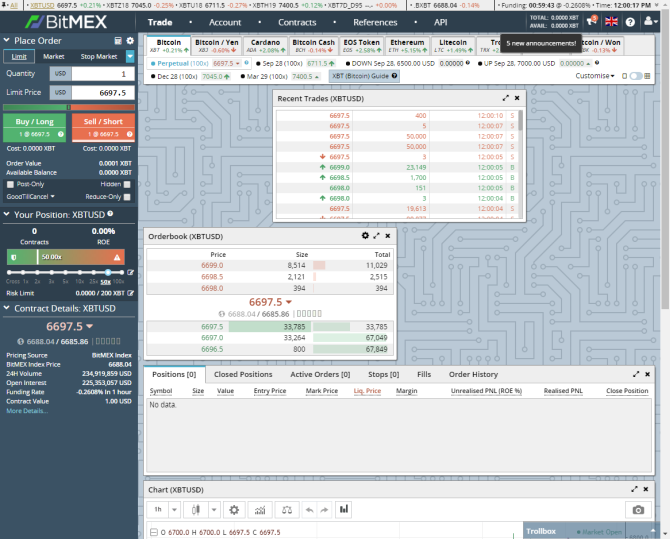
Think you’re getting the hang of Spark Profit? Why not step up to the next level with a Bitmex Testnet account? Bitmex is one of the most popular crypto exchanges. Here, you take a long or short position on where one of the listed cryptocurrencies will be in a certain time frame. Then, you apply leverage. Leverage can boost your potential profits (or losses) by up to 100 percent.
You will need to grab some Testnet Bitcoin from a faucet (follow the Bitmex tutorial to find out how), but then you can begin trading using the Bitmex Testnet. It’s valuable education before attempting to trade crypto futures!
What’s the Best Bitcoin Beginner’s Tip?
Education. All the way. If you don’t educate yourself before opening your wallet, you’re best off heading to the nearest bathroom and flushing your dollars straight away. Save yourself the time.
Trying out cryptocurrency trading in a mock market is a great first step. Reading articles, blog posts, and more helps, too. But at some point, you’re going to have to take the first step. Start small, and most of all, move slowly.
Read the full article: The 7 Best Risk-Free Cryptocurrency Trading Simulators
from MakeUseOf https://ift.tt/2Dq47lv
via IFTTT